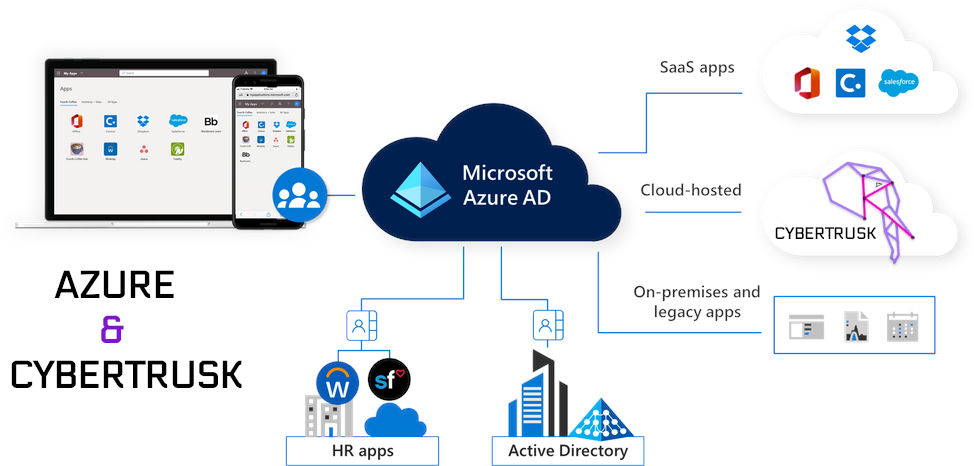
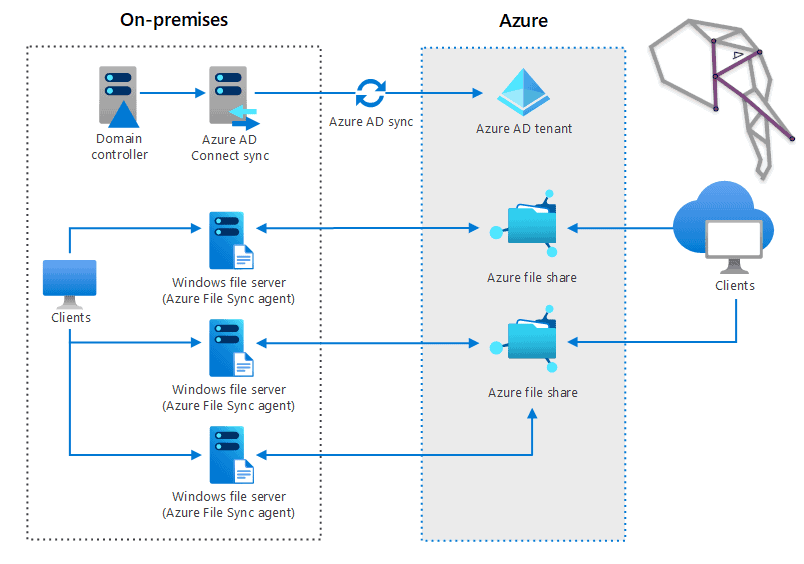
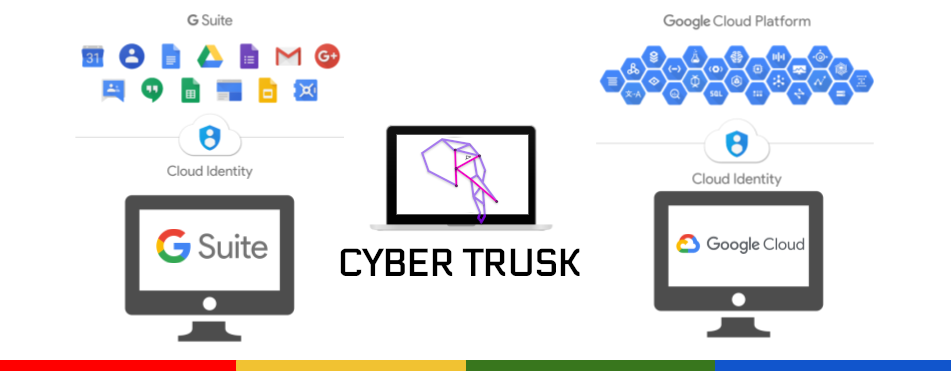
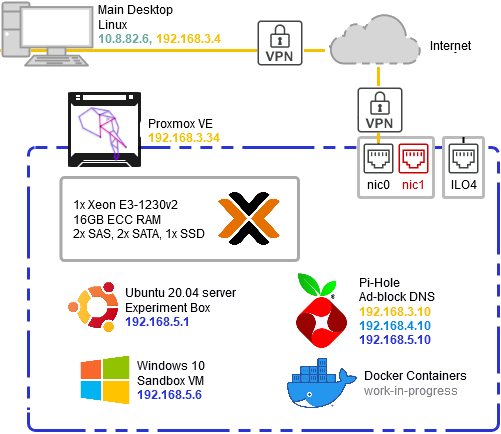
About Us
If you are looking for secure, reliable and dedicated servers with a lot of resources and top quality availability Cyber Trusk is the solution.
Located in Bangkok, Thailand with multiple datacenters our security experts will help you make the right technological decisions.
- Reliable: 99.999% Uptime Guaranteed
- Secure: Physical Segregation
- Cost effective
We help you digitalize your business leveraging the cloud technologies to make your business thrive. Our Cloud environments are not shared but dedicated servers and infrastructure per client for a better level security and total data privacy.
Order Now
Happy Clients Our team of experts already designed and implement secure cloud infrastructures.
Projects All your company's business units will gain in efficiency through digitalization.
Years of experience In IT infrastructure an cyber Security are combined in the team
Certifications Our experts cumulate more than 13 Internationally recognized certifications (AWS, Azure, CREST, CISSP, ISO, GWAPT, GPEN, Microsoft Certified, ...)
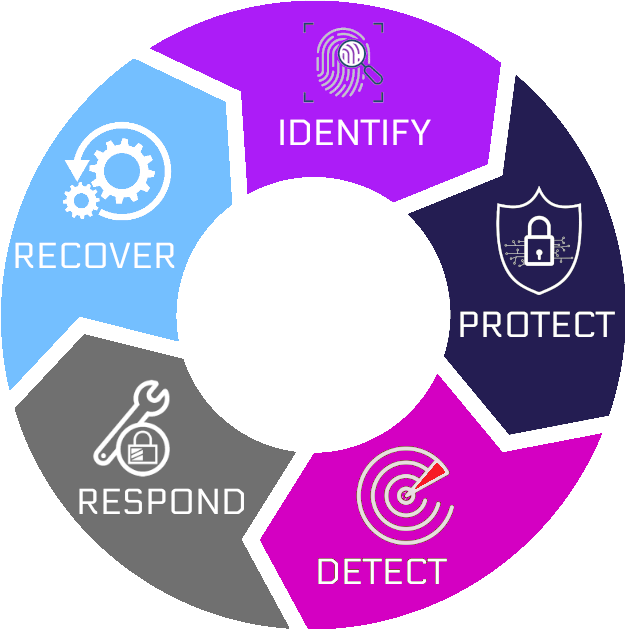
Security Operating Center (SOC)
All our expertise to secure your business
Consulting
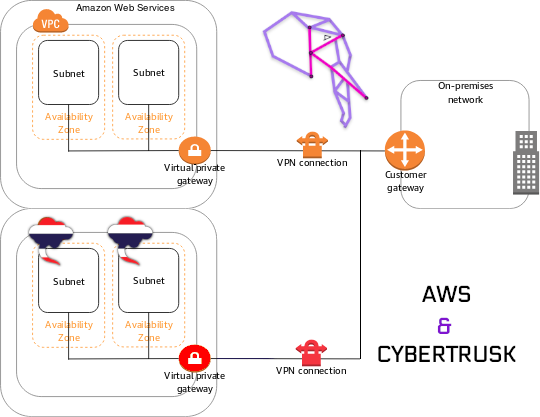
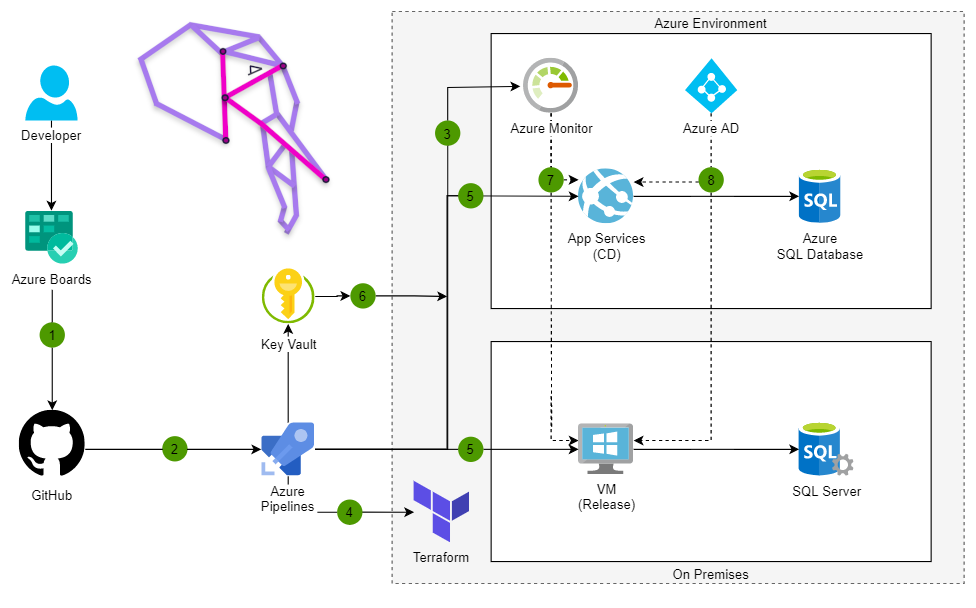
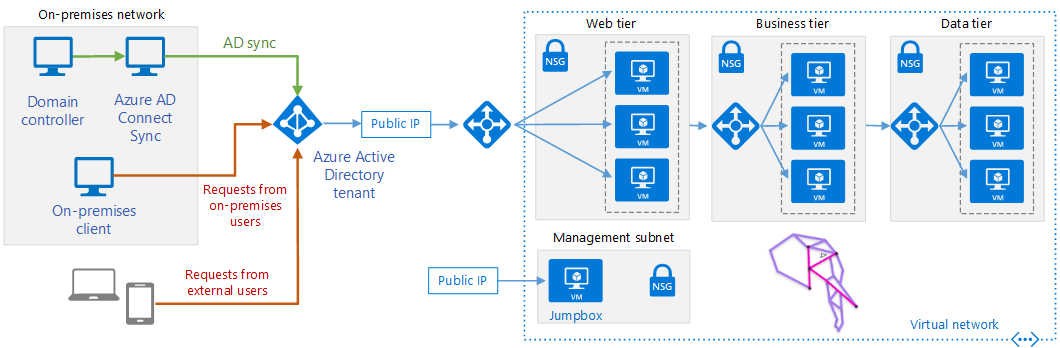
The following secure cloud architecture have been deployed for our clients
- All
- Site-to-Site
- Full-Cloud
- Hybrid
Training
Certified professionals at your service
Certifications
We accompany you toward the implementation of the state-of-the-art security standards for certifications or audits.
Boost your business
Our experts can design and implement the right tools and ifrastructure for a successful digitalization or your company.
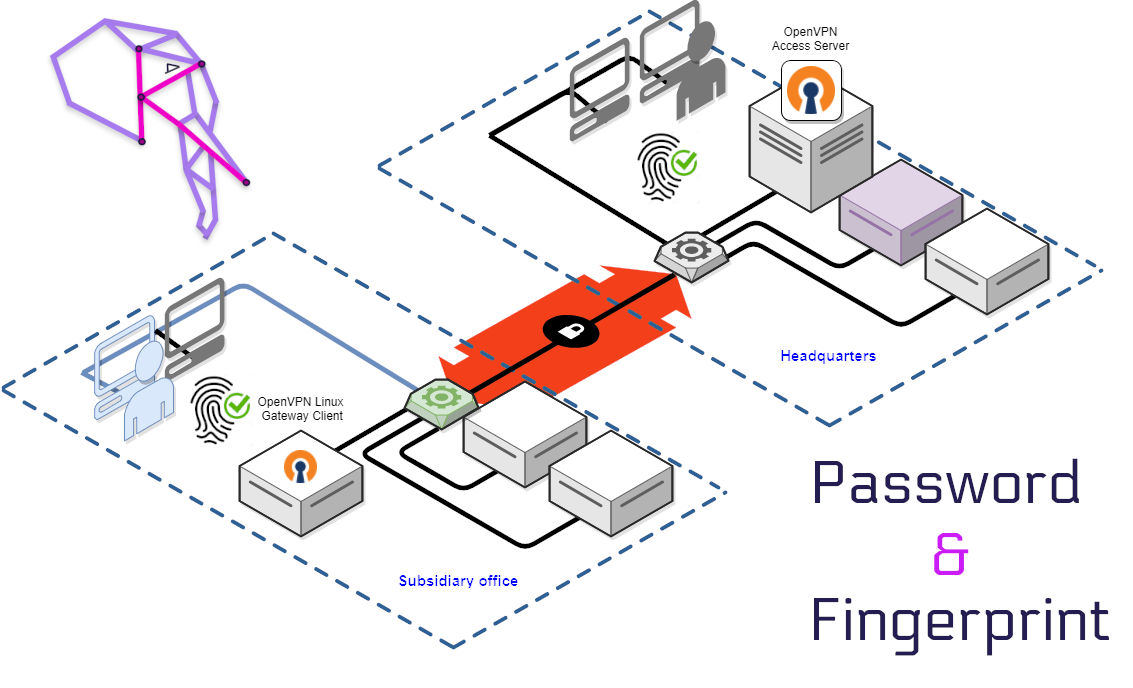
World-Wide Secure Networks
Remote working is the futur! Deploy Point-to-Point Multi Factor Authentication VPN between all your business locations and for all your employees.
Solutions
Trust in Innovation & Automation
Cloud offers - Security as a Service
All prices below are estimations (based on previous realized projects)
Starter / 1 Secure Site + 10 Users
$55 / month
- Dedicated Hardware
- Private VPN
- 2 Factors Authentication
- Encrypted Backups
Advanced / 5 Sites + 20 users
$220 / month
- Starter options
- XDR and Antivirus
- SOC monitoring
- 1 Pentest per year
Optimal / >5 Sites + >20 Users
$Contact Us
- Advanced options
- Process and Procedure redaction
- Security awarness, including phishing
- Guidance toward Certification
Features
Some Technical Features we deployed for our clients
Frequently Asked Questions
Why dedicated hosting is better than shared?
Dedicated hosting means your website is hosted on a single server that is dedicated specifically to your website. This cuts out the competition of resources associated with shared hosting, and results in more robust website performance and stronger security.
How often should you backup your Data?
Important data should be backed up at least once a week for cold storage and daily for hot storage. These backups can be performed manually or automatically. A lot of software options are available for hot backup that can save your data every day only taking differences to save disk storage.
Why physical security is important?
Physical security is about keeping your facilities, people and assets safe from real-world threats. It includes physical deterrence, detection of intruders. Having efficient countermeasure in place is mandatory to keep your data safe from any threats (Secure rooms, CCTV, strong encryption mechanism, DLP, ...)
Is my password strong enough?
No! A simple password is not strong enough no matter the size. Every system should use 2 factors authentication.
Contact Us / Order
Cyber Trusk is offering secure and affordable cloud environments on Thailand based Dedicated Servers. For every business to thrive and operate remotely thanks to cloud technologies.
Pridi Banomyong 20/1 Alley
Sukhumvit 71 Rd, Watthana, Bangkok
contact@cybertrusk.com
LINE ID: cybertrusk